Before, during, and after a cybersecurity incident, professionals at any security operations center (SOC) have their hands full with an array of threat mitigation, detection, and recovery tasks. They typically don’t have time to download data from threat profile databases, or do extensive scans and searches of online threat repositories. What’s needed are security orchestration, automation, and response (SOAR) capabilities that effortlessly integrate with other information security (IS) platforms. In today’s highly susceptible cyber world, nothing but the best SOAR platform can seamlessly deliver those objectives.
The Need of the Hour
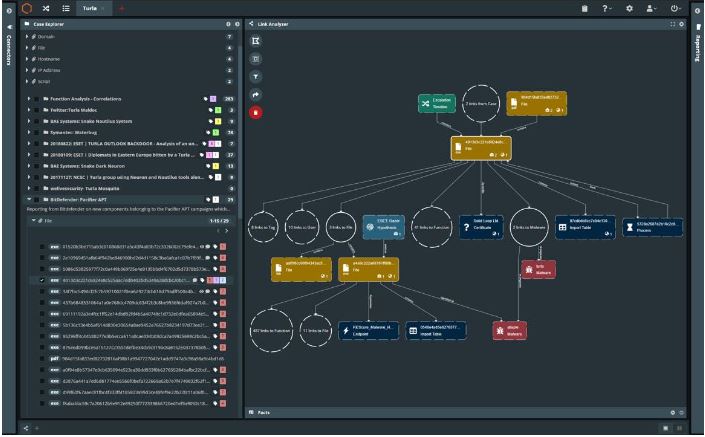
The need of the hour is a highly-intuitive, well-designed, intelligent Security Operations Platform (SOP), that empowers cyber incident response (IR) teams with powerful information and data sharing capability. Without that ability, response teams function reactively, and are like a pilot “flying blind” in the dark, when all cockpit instruments have failed.
For many, if not most, organizations, collaborating seamlessly to detect, prevent, and recover from cyberthreats, is a major impediment to cybersecurity. In the absence of a robust SOAR cyber security platform:
– Internal cybersecurity capabilities tend to compartmentalize, creating silos of data and information that no one else has knowledge of, or access to
– Cooperation with external partners, including infrastructure vendors, cybersecurity consultants, and outside threat intelligence (TI) service providers, is severely limited
To bring efficiency to any organizations’ cybersecurity efforts, it’s important to break down these barriers. Implementing the best SOAR platform not only tears down the walls of information silos within the organization, but it also aids in seamless and timely communication with 3rd-party partners, as well as in working to report and respond to regulators’ concerns and requirements around cyber incidents and preparedness.
Empowering Incident Response (IR) Teams
IR teams have an uphill challenge – that of bringing a wide-ranging team of cybersecurity specialists together, to accomplish a full cycle of activities within the shortest possible time. With all that’s on their plate, existing threat assessment and response frameworks, from monitoring to remediation, add needless complexities to an IR team’s mission. The dilemma is:
– A well-planned incident response requires time. Collecting, analyzing, assessing, and responding to a threat (or preventing one) may provide bad cyber actors additional time to wreak havoc on an organization’s data assets
– A hasty and immediate response, on the other hand, without the benefit of a well-thought-out plan, may be equally devastating. Action, without the insight of actionable analytics may even help, rather than hinder, the objectives of cybercriminals
QuoLab has designed its SOAR cyber security platform to overcome these challenges. No longer will cybersecurity teams respond to the threat landscape using a linear approach. Instead, the Platform provides IR teams a highly innovative set of tools to work collaboratively, and in parallel, to acquire and fuse data sets to support each other for targeted and effective incident response.
In a rapidly evolving cyber world, flexibility is the key to effective incident response. IR teams require the right data, at the right time, and wrapped around the right analytical framework. Whether it’s access to emerging threats, alerts on imminent attacks, or monitoring ongoing threat landscapes around the world, the Platform’s uniquely target-centric case model empowers IR teams by delivering proactive TI to them.